January 2, 2026
Categories:
When Your Phone Number Turns Against You: Inside the SIM-Swap Scam

Imagine waking up one morning to find your phone has no signal. Hours later, your email is locked, your bank sends fraud alerts, and your crypto wallet is empty. This isn’t a movie plot; it’s one of the fastest-growing cybercrimes in the world. And while most of us think two-factor authentication protects us, criminals have found a backdoor - It starts with your phone number.
What Is the SIM-Swap Fraud and How Does It Happen?
This type of fraud doesn’t have one official name, but investigators usually call it SIM-swap fraud or mobile identity hijacking. At its core, the scam relies on a simple weakness: mobile numbers can be transferred (“ported”) between carriers. If scammers trick a telecom operator into moving your number to their SIM card, they instantly gain access to all the services tied to it, from banking to crypto to social accounts.
Confirmed Damage from the SIM-Swap Fraud
SIM-swap fraud first appeared clearly in FBI statistics from 2018 onward. The FBI’s Internet Crime Complaint Center reported 320 SIM-swapping complaints and about $12 million in losses between January 2018 and December 2020, rising to 1,611 complaints and more than $68 million in 2021 alone. Additionally, 2025 fraud analysis estimates that FBI-investigated SIM-swap attacks in 2023 alone caused nearly $50 million in losses and about $26 million in 2024.
Here are some of the recent individual cases showing how the numbers translate into real damage:
O2 customer in the UK, 2025: An O2 customer discovered that her long-time mobile number had quietly been moved to a SIM controlled by someone else. Her phone still looked normal, but calls and texts were redirected to the attacker. Within hours, unfamiliar credit-card charges appeared, and every attempt to log into online banking failed, because all verification codes were now going to the fraudster. By the time the situation was finally reversed, £4,500 had been taken, and she had to go through a full rebuild of her banking access and security settings.
EE customer in the UK, 2025: An EE customer received a text saying a new SIM for her number had been activated. She hadn’t requested anything, so she called support straight away and begged them to block any change. Twenty-four hours later, her phone went dead anyway. The attacker, now holding her number, methodically reset login details to shopping accounts, banking apps and email accounts. Savings were moved, purchases were made, and two long-standing email addresses tied to her identity were locked away forever, because the attacker used SMS-based two-factor to seize them first.
WECOM customer in Israel, 2025: A young mother suddenly started receiving messages that her mobile line was being transferred away from her current operator, followed, moments later, by a “welcome” SMS from a different provider she had never contacted. Shortly after, her phone lost service entirely - but her number was active on a criminal’s device. While she tried to reach support from another phone, the attacker used the hijacked line to receive banking one-time codes, change passwords and initiate fraudulent card and account activity. Only rapid calls to her carrier, banks, and card issuers stopped the damage from spreading further.
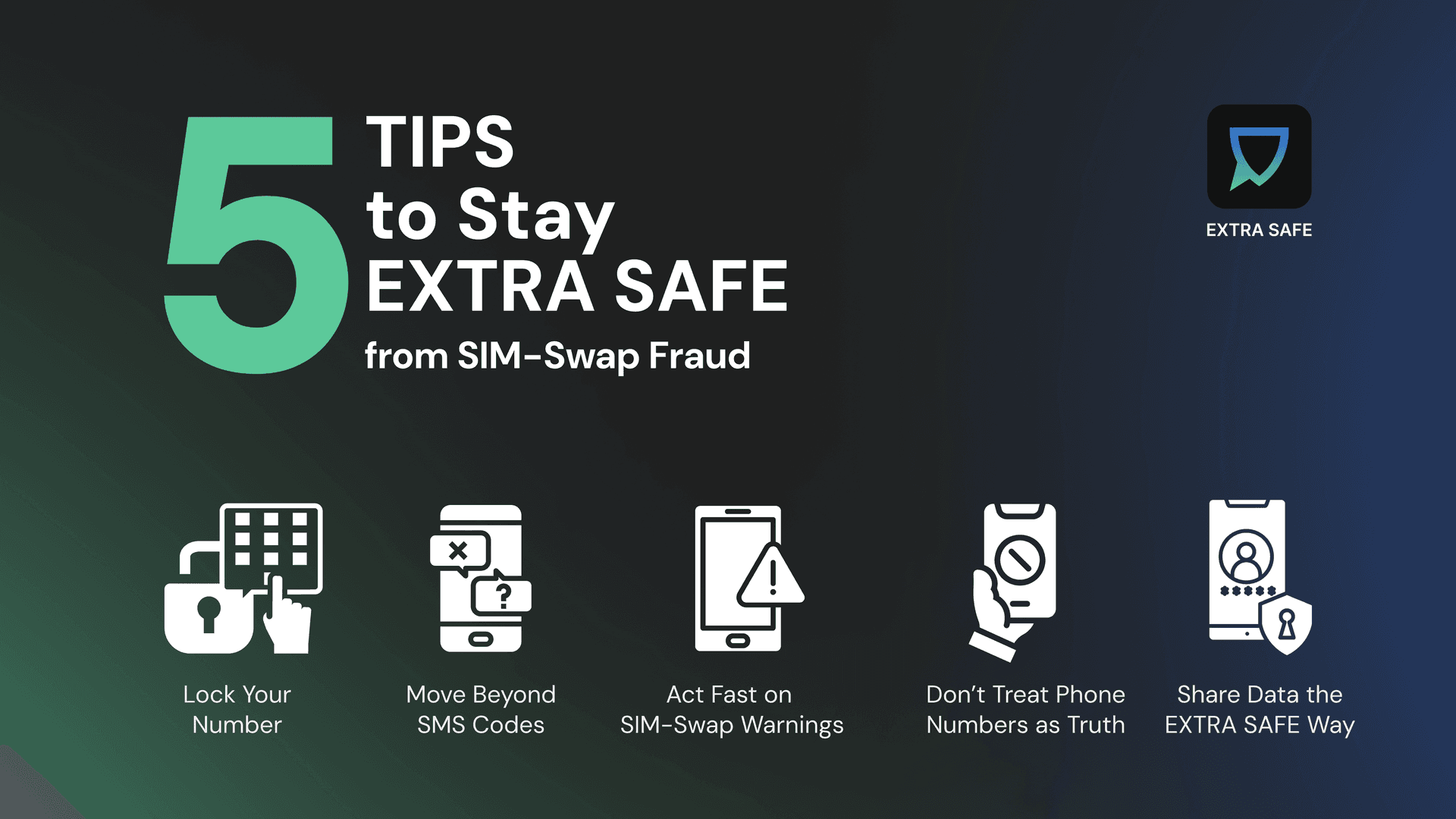
5 Tips to Stay EXTRA SAFE from SIM-Swap Fraud
1.
Put a lock on your number: Ask your mobile provider to add the strongest possible protection to your account: a port-out PIN, “SIM change” password, or equivalent lock that must be confirmed before your number can be moved. Regulators like the FCC in the US and ACMA in Australia explicitly require carriers to use stronger identity checks for SIM changes and port-outs, because weak checks are a known path for SIM-swap fraud.
2.
Don’t rely on SMS codes for your most important accounts: Wherever you can, replace SMS codes with app-based authentication (like an authenticator app) or hardware security keys for email, banking, brokerage, crypto, and password managers. SMS is weaker as phone numbers can be taken over, while app or key-based factors are much harder to steal remotely.
3.
Treat warning signs as an emergency, not an inconvenience: If your phone suddenly loses service where it normally works, or you get messages about a SIM change, eSIM activation or port-out you didn’t request, act immediately: call your provider from another phone, tell them you suspect SIM-swap, and contact your bank and card issuers to flag possible fraud. Fast reaction is critical: once criminals control your number, they can intercept two-factor codes and drain accounts in minutes.
4.
Stop treating your phone number as a single source of truth: If you design or run systems, treat a recent SIM swap or port-out as a high-risk signal, not as a neutral event. Combine phone intelligence (recent SIM change, number age, port history) with additional checks for high-risk actions like password resets, device enrollment, or changing MFA methods, instead of trusting SMS alone.
5.
Share your number and other sensitive data only through safe platforms like EXTRA SAFE: Most SIM-swap attacks start with personal data + phishing. Don’t post your main phone number publicly if you can avoid it, and be extremely cautious about responding to requests asking you to “verify” personal or account details. Whenever you need to share your number or any sensitive data about yourself, use secure P2P apps like EXTRA SAFE, which don’t store or track your data, so your conversations stay truly private and secured with asymmetric encryption. In addition, EXTRA SAFE works without your phone number, so your identity stays fully private.
Try it directly from your browser at extrasafe.chat
Prefer mobile? Download the EXTRA SAFE app for iOS and Android.