December 17, 2025
Categories:
How Messaging Apps Store Your Data — and Why It Matters More Than Ever
Article written with ChatGPT AI
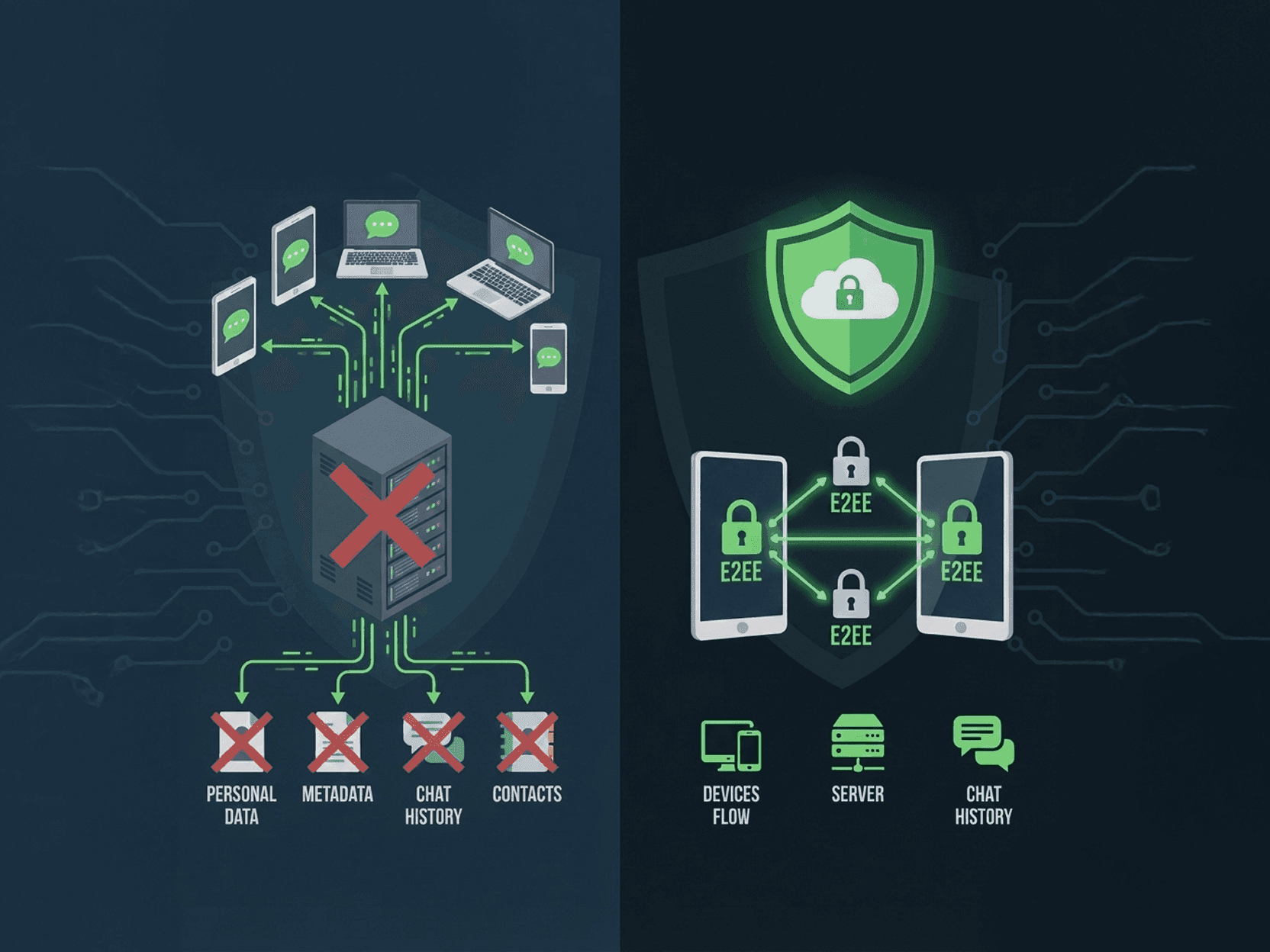
This article explains how popular messaging apps store, retain, and process user data — and why those practices matter in an era of frequent data leaks and growing surveillance. It shows where users can find and understand data-handling policies, compares EXTRA SAFE with WhatsApp, Telegram, and Signal across identity, metadata, retention, and encryption models, and outlines real-world scenarios where privacy risks are highest.
*Resume created with artificial intelligence
Over the past few years, data leaks, account takeovers, and large-scale exposure of private communications have stopped being rare headlines. They’ve become background noise. For everyday users, this raises an uncomfortable question: what actually happens to your messages, calls, and files after you hit “send”?
Most people choose messengers based on convenience or popularity, not on how data is stored, retained, or analyzed behind the scenes. Yet these technical details define how exposed your conversations really are — not only to hackers, but also to internal access, third-party services, and long-term data retention policies.
In this entry, we’ll explain how popular messaging apps approach data storage and protection, where users can find this information, and how these models compare to EXTRA SAFE’s privacy-first design.
Why Private Conversations Don’t Stay Private
High-profile data exposures have repeatedly shown that encryption alone doesn’t eliminate risk. Messaging platforms and email services have faced incidents involving leaked cloud backups, scraped contact graphs, exposed metadata, compromised admin tools, and improperly secured archives.
Even when message content remains encrypted, associated data — who you talk to, when, how often, from where, and on which devices — often remains stored. In some cases, chat history is retained indefinitely unless users manually change settings. In others, backups are enabled by default and protected by weaker safeguards than live conversations.
The key risk isn’t just interception. It’s persistence. Data that exists can be accessed, requested, breached, or misused later. Understanding how and where this data lives is essential for anyone who values long-term privacy — not just for activists or businesses, but for families, freelancers, and everyday users.
How to Understand a Messenger’s Data Practices
Every major messaging app publicly documents how it handles user data — but rarely in one simple place.
Users can typically find relevant information in:
Privacy policies (data collection and retention)
Security or encryption whitepapers
Help center articles on backups and device syncing
GDPR or regional compliance disclosures
Transparency reports and law-enforcement guidelines
What to look for:
Whether identity is tied to personal data (phone number, email)
What metadata is collected and how long it’s stored
Whether chat history is retained by default
How backups work and where they are stored
Whether calls are routed through centralized infrastructure or directly between devices
Reading these documents doesn’t require legal expertise — just attention to what’s kept, for how long, and under whose control.
How EXTRA SAFE Compares to Popular Messaging Apps
Aspect |  EXTRA SAFE |  |  Telegram |  Signal |
|---|---|---|---|---|
Identity model | Anonymous in-app identifier | Phone number-based | Phone number-based | Phone number-based |
Call architecture | Device-to-device (P2P) | Server-assisted | Server-assisted | Server-assisted |
Encryption | End-to-end asymmetric encryption | End-to-end (chats & calls) | Client-server by default | End-to-end |
Metadata handling | Minimal, session-based | Stored for operations | Stored extensively | Limited but present |
Chat history retention | Clears by default | Stored unless deleted | Stored in cloud by default | Stored on device |
Backup exposure | Session-based, ephemeral | Optional cloud backups | Cloud-native | Device backups |
Important note: Every call in EXTRA SAFE connects device-to-device (P2P) and is protected with blockchain algorithms. EXTRA SAFE uses end-to-end asymmetric encryption across communication sessions.
When EXTRA SAFE Is the Best Choice
1. Business Communication
Main risk: Long-term storage of sensitive discussions, files, or negotiations.
How EXTRA SAFE helps: P2P calls, session-based chats, and end-to-end asymmetric encryption reduce data persistence while protecting shared business content.
2. Family & Private Sharing
Main risk: Personal media and conversations lingering in backups or cloud storage.
How EXTRA SAFE helps: Temporary communication sessions and minimized retention keep private moments private.
3. High-Risk Environments
Main risk: Metadata exposure in regions with surveillance, censorship, or conflict.
How EXTRA SAFE helps: Anonymous identity handling and device-to-device communication reduce traceability.
4. Short-Term Sensitive Collaboration
Main risk: One-off discussions leaving permanent digital traces.
How EXTRA SAFE helps: Communication designed to exist only for the duration it’s needed.
5. Privacy-First Professionals
Main risk: Accidental data accumulation across tools.
How EXTRA SAFE helps: Clear, predictable data behavior aligned with modern privacy expectations.
Final Thought
Encryption is essential — but it’s only part of the privacy equation. How long data exists, what metadata is stored, and how identities are handled matter just as much.
EXTRA SAFE is built around temporary, device-to-device communication. Every call connects device-to-device (P2P) and is protected with blockchain algorithms. EXTRA SAFE uses end-to-end asymmetric encryption, aligning security with minimal data retention by design.
Try It Now
If your conversations matter, start them in a space designed to keep them truly private. Start with EXTRA SAFE.